The communication landscape in 2026 is defined by a profound shift from the traditional “information age” into what global analysts term the “Intelligence Age”. For communications leaders, the proliferation of digital data has rendered manual oversight obsolete, as the sheer volume of narratives across traditional editorial news, social platforms, and generative search engines requires a level of processing speed that only artificial intelligence can provide. Organisations are no longer merely placing scattered bets on emerging technologies but are deeply embedding AI media monitoring tools into their core workflows to scale their strategic investments and drive measurable business outcomes.
What Are AI Media Monitoring Tools?
AI media monitoring tools are integrated intelligence platforms that leverage advanced natural language processing, machine learning models, and generative AI to automatically identify, categorise, and evaluate media coverage across a global spectrum of channels. In 2026, these tools have moved beyond simple keyword-matching systems to become sophisticated “External Intelligence” modules that provide context-aware analysis of a brand’s reputation. They function by capturing data from millions of sources—including 30,000+ newspapers, 3 million+ news sites, 12,000+ broadcast stations, and thousands of podcast titles—standardising this information within seconds of publication.
The fundamental difference between traditional media monitoring and modern AI tools for media monitoring lies in the transition from reactive tracking to proactive intelligence. Traditional systems operated on static Boolean searches, delivering a “clipping” service that documented past mentions. Conversely, best AI media monitoring software in 2026 utilizes semantic understanding to interpret the “why” behind conversation spikes, identify narrative drift, and predict future reputational trajectories before they impact the bottom line.
For the purpose of strategic alignment, AI media monitoring tools can be defined as follows:
Strategic AI media monitoring tools are purpose-built intelligence suites designed to synthesise billions of disparate data signals into cohesive narrative perspectives, enabling communications professionals to map stakeholder dynamics, anticipate story momentum, and measure the authentic impact of their engagement strategies against organisational goals.
How AI Has Changed Media Monitoring in 2026
The year 2026 represents an inflection point for the communications industry, where AI has evolved from a novelty assistant into the “operating system” for successful public relations teams. This transformation is characterised by several key technological shifts that have redefined the scope of media intelligence.
Predictive vs. Reactive Alerting Mechanisms
Historically, the value of a monitoring service was measured by its “speed to alert.” In 2026, the focus has shifted to “speed to foresight”. Predictive media monitoring platforms now use historical pattern analysis and growth velocity indicators to model the potential reach and engagement of a developing story. This allows teams to identify whether a trend is in a catalyst phase, a virtuous circle, or nearing its peak, facilitating more effective timing for media outreach or crisis mitigation. Predictive KPIs now allow for 90-day forecasting of hits, reach, and engagement metrics with high statistical accuracy.
Narrative Clustering and Semantic Mapping
The fragmentation of the media landscape into niche forums, social channels, and traditional editorial outlets has made it difficult to see the “big picture” through individual mentions. Narrative intelligence software now uses semantic AI to cluster raw data into cohesive “Stories” and “Perspectives”. This provides a high-level view of how different stakeholder groups—such as regulators, consumers, or technical communities—are framing a brand’s actions. By mapping these narrative arcs, communications leaders can detect the precise moment a strategic opportunity begins to shift toward a reputational risk.
Generative AI Summarisation and Assistant Workflows
Generative AI in communications has automated the most time-consuming aspects of the PR workflow: the analysis and summarisation of large datasets. Features like conversational AI assistants allow users to query their media data using natural language, asking questions like “What are the primary drivers of our negative sentiment in the APAC region this week?”. These tools instantly generate executive-ready intelligence digests that explain the story behind the numbers, reducing the reliance on manual reporting and spreadsheets.
Multi-Stakeholder Intelligence and Mapping
Media monitoring in 2026 has expanded its aperture beyond customers to encompass a “360-degree view” of the entire stakeholder ecosystem. Stakeholder intelligence platforms now continuously track perceptions among employees, investors, regulators, and the general public, connecting these perceptions to actual behaviours such as purchase intent or recommendation rates. This allows corporate affairs and ESG leaders to prove their impact with credible, stakeholder-driven data rather than isolated media metrics.
Misinformation Detection and Narrative Integrity
In an era of deepfakes and synthetic content, maintaining “narrative integrity” has become a central challenge for communications professionals. Best AI media monitoring software now includes specialized modules for detecting unusual patterns in content propagation, flagging potential bot-driven misinformation campaigns before they reach mainstream audiences. These systems filter out noise and “AI slop,” ensuring that communications teams respond only to genuine signals that could impact brand trust.
Broadcast Transcription and Multimedia Intelligence
Traditional monitoring often struggled with non-textual data, but the 2026 suite of tools uses advanced vision encoders and automated speech-to-text (ASR) to monitor 12,000+ broadcast sources and 70,000+ podcast titles in real-time. AI-powered logo recognition and scene detection allow brands to track their visual presence in video content, even when they are not mentioned by name. This “multimodal” capability is essential for founders and enterprises alike who wish to dominate both human attention and AI knowledge graphs.
AI-Assisted Measurement and ROI Frameworks
The move toward AI in PR has finally enabled the industry to move past outdated metrics like Advertising Value Equivalency (AVE) toward sophisticated impact measurement. By aligning media data with business KPIs—such as lead generation, website traffic, or sentiment shifts within a specific regulatory segment—AI tools provide a clear link between communications activity and business growth. These systems are designed to comply with the AMEC Integrated Evaluation Framework, ensuring that measurement is strategic and outcome-oriented.
| Monitoring Capability |
Traditional Method |
AI-Driven Method (2026) |
| Alerting |
Reactive (Keyword triggers) |
Predictive (Pattern & velocity triggers) |
| Context |
Manual review |
Automated narrative clustering |
| Data Scope |
Editorial and major social |
Omnichannel including LLM outputs & podcasts |
| Sentiment |
Positive/Negative/Neutral |
Contextual emotion & intent analysis |
| Reporting |
Static periodic reports |
Real-time narrative summaries & AI assistants |
| Measurement |
Outputs (Mentions, Reach) |
Outcomes (Sentiment shift, Behavioural change) |
How to Evaluate AI Media Monitoring Software
With the market for AI tools for media monitoring becoming increasingly saturated, communications leaders must apply a rigorous evaluation framework to ensure they select a platform that offers genuine strategic value rather than just “flashy demos”.
Predictive Intelligence and Forecast Accuracy
The most critical factor is the platform’s ability to turn historical data into forward-looking intelligence. Evaluators should ask for evidence of a tool’s “90-day forecasting” accuracy and its ability to identify “spike detection” before the event reaches a mainstream threshold. High-performing systems use trillions of data points to train their models, ensuring that predictions are grounded in reality.
Narrative Detection and Clustering Sophistication
Effective narrative intelligence software must be able to group related mentions into high-level “Stories” while identifying the different “Perspectives” within them. This goes beyond basic tagging; it requires a deep semantic understanding of how themes are evolving and which influential voices are shaping the discourse. The tool should be able to distinguish between different types of mentions—such as a developer discussing a repository on GitHub versus an investor commenting on a financial forum.
Public Affairs and Regulatory Integration
For organisations in regulated sectors like finance, healthcare, or energy, the integration of public affairs data is essential. The platform should monitor legislative sessions, regulatory change, and political influencer activity alongside editorial news. A unified view that connects media sentiment with political developments allows for a more comprehensive assessment of reputational risk.
Measurement and ROI Framework Alignment
Communications leaders should prioritise platforms that facilitate measurement based on the AMEC Integrated Evaluation Framework. This includes the ability to set synergistic objectives, conduct baseline measurements, and track outcomes and impact rather than just outputs. Features like “PR Custom Scoring” and “Website Traffic Insights” through UTM links are vital for proving the ROI of communications efforts to the C-suite.
Regional Data Depth and Multilingual Support
Global organisations require a platform with deep regional coverage and the ability to process data in local languages. In 2026, this means more than simple translation; it requires a “cultural anchoring” that understands the nuance of local media landscapes, particularly in complex regions like APAC or the Middle East. Check for localized interfaces and support in languages such as Korean, Simplified Chinese, and Traditional Chinese.
Multimedia and Multimodal Coverage
The modern media landscape is increasingly audio-visual. Evaluation must include the platform’s ability to monitor 12,000+ broadcast sources, 25,000+ podcasts, and visual-first social channels like TikTok and Instagram. Proprietary logo recognition that can detect 30,000+ brand logos in video frames is a benchmark for top-tier visual analytics.
Human Oversight vs. Full Automation
While AI handles the high-volume “grunt work,” human expertise remains the “compass” that provides context and sincerity. The best platforms offer a hybrid service model—managed monitoring with expert curation for high-stakes reports, combined with self-service dashboards for day-to-day tracking.
| Evaluation Metric |
High-Maturity Platform |
Basic Monitoring Tool |
| Forecasting |
Predictive KPIs |
No predictive capability |
| Narrative Tracking |
Clusters data into “Stories” |
Simple keyword lists |
| Stakeholders |
Maps multiple stakeholder groups |
Focuses only on consumers |
| AI Access |
Tracks brand presence in LLMs |
No LLM/AEO visibility |
| Multimedia |
Real-time TV/Radio & Podcasts |
Text-only or delayed broadcast |
| Integration |
Connected to CRM & Public Affairs |
Siloed data |
Top 10 AI Media Monitoring Tools in 2026
The following ranking represents the best AI media monitoring software available in 2026, categorised by their primary strengths and suitability for different strategic objectives.
1. Vuelio
Vuelio is positioned as the definitive “organisational story-management platform,” making it the top choice for communications leaders who require a unified view of politics, editorial news, and social media. It is particularly strong for public affairs teams and organizations operating in the UK and European markets, where the intersection of government policy and media narrative is most critical.
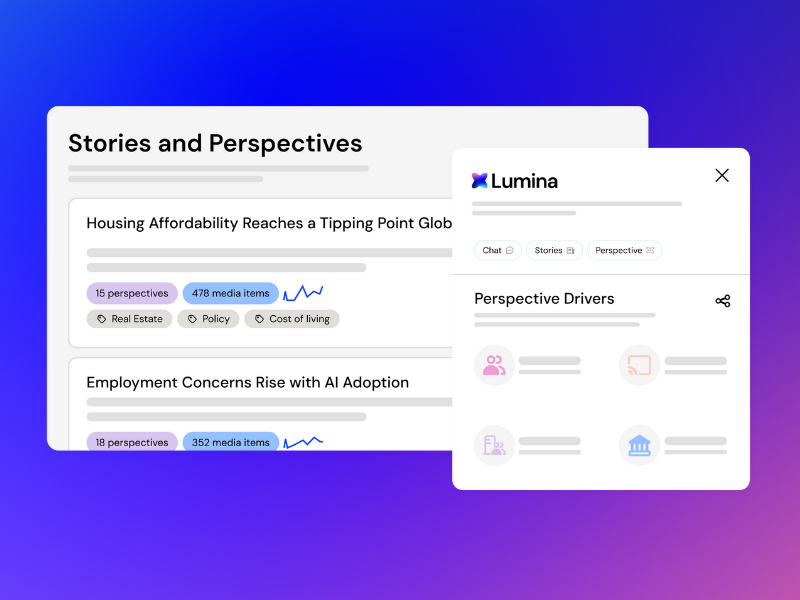
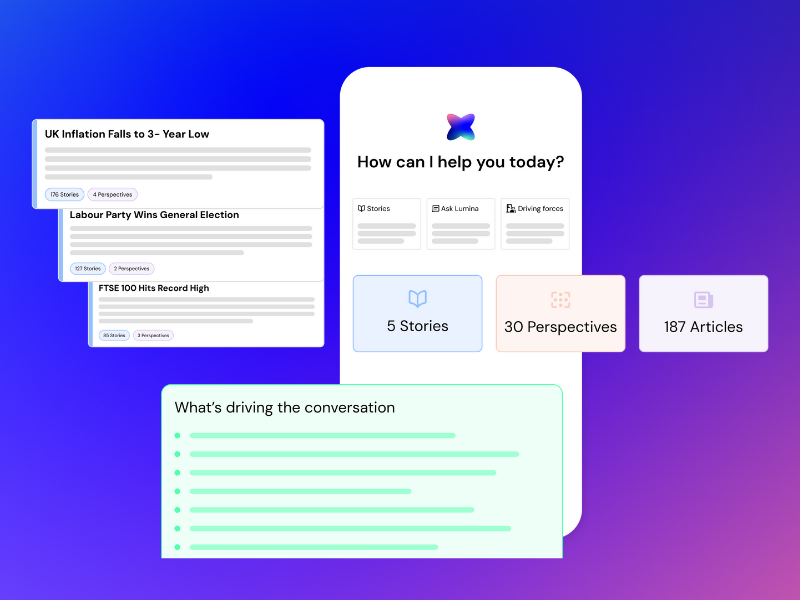
Vuelio started 2026 by bringing in its groundbreaking Lumina AI suite. Lumina is specifically designed to shift PR and communications professionals from passive monitoring into the role of strategic pacesetters.
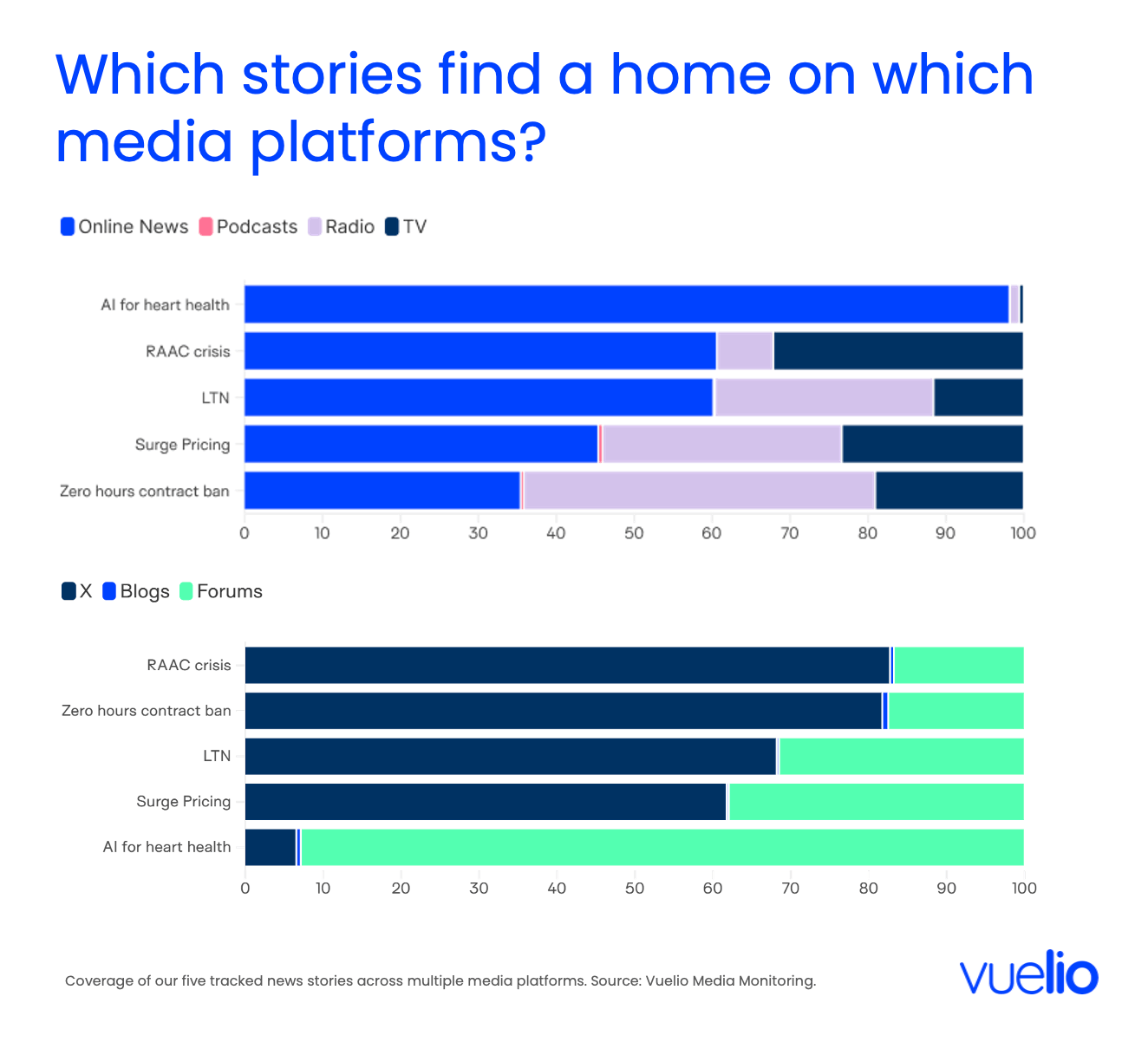
The Lumina suite is trained on the actual workflows of modern communications, focusing on enhancing message clarity and early risk detection. Its Stories & Perspectives module is a 2026 benchmark for narrative intelligence software, clustering millions of data points into cohesive high-level topics while identifying the distinct audience and public affairs angles within them.8 This allows leaders to rise above the noise and identify which topics are gaining momentum and which influential voices are shaping the discourse.
Vuelio’s 2026 suite focuses on providing “actionable intelligence” to help organisations make their story matter in an age of information overload. It features the industry’s most powerful media list, providing direct access to over one million journalists, MPs, expert bloggers, and influencers from nearly 200 countries. This database is editorially verified and constantly updated, ensuring that teams always reach the right people for their campaigns. The platform also includes comprehensive monitoring for broadcast, print, online, and social media, providing real-time feedback to refine communication strategies.
Key Advantages for 2026:
- Lumina AI Suite: Purpose-built for PR and public affairs to map narrative trajectories.
- Public Affairs Integration: Specialized tools for tracking political activity, MPs, and legislative shifts.
- Comprehensive Media Database: Access to 1 million+ verified profiles with deep filtering capabilities.
- Evaluation and Analytics: Real-time reporting on reach, impressions, and message pull-through.
Vuelio is ideally suited for teams that need to manage complex corporate reputations and navigate public affairs alongside traditional PR activity.
2. Cision
Cision remains one of the largest all-in-one PR platforms globally, and in 2026 its CisionOne suite continues to position itself as an end-to-end communications operating system. Its scale is considerable, with a vast journalist database and integrated distribution via PR Newswire.
However, that breadth is also where trade-offs begin to emerge. The platform’s AI capabilities—while robust in terms of automated summaries, monitoring, and dashboarding—are heavily oriented toward workflow efficiency rather than deep narrative interpretation. The CisionOne React Score, for example, provides real-time performance indicators, yet these metrics can prioritise volume and visibility over contextual nuance.
For large enterprise teams, complexity can also be a constraint. The integration of distribution, monitoring, and measurement into a single ecosystem may reduce vendor fragmentation, but it can introduce operational heaviness. Public affairs integration, particularly parliamentary and stakeholder relationship mapping, is not as deeply embedded as in platforms purpose-built for regulated environments.
Summary: Comprehensive and scalable, but stronger on operational breadth than strategic narrative or public affairs intelligence.
3. Meltwater
Meltwater’s positioning around “Outside Insight” and its GenAI Lens feature reflects an ambitious attempt to capture the AI media monitoring narrative. The GenAI Lens, which tracks how brands appear within LLM-generated responses, is a forward-looking feature in the age of generative search.
Yet the platform’s scale—spanning hundreds of thousands of news sources and multiple social channels—can introduce signal dilution. Large volumes of automated insight do not necessarily equate to strategic clarity. The Mira Studio assistant provides generative summaries, but like many AI-driven tools, it risks flattening complex stakeholder dynamics into digestible yet simplified narratives.
Integration across media, social, and consumer intelligence is technically impressive, but organisations operating in public affairs-heavy or highly regulated sectors may find the platform less tailored to political monitoring or legislative tracking. As enterprise deployments grow, cost structures and configuration complexity can also become a consideration.
Summary: Powerful in scale and LLM visibility, but volume-led intelligence may require significant interpretation to support nuanced public affairs strategy.
4. Talkwalker (by Hootsuite)
Talkwalker’s Blue Silk AI engine is frequently cited for its emotion analysis and predictive modelling capabilities. Its visual recognition system—capable of detecting thousands of brand logos in images and video—makes it particularly appealing to global consumer brands.
However, its strength in visual and social listening does not always translate into equivalent depth in stakeholder intelligence or political risk analysis. The predictive modelling tools focus primarily on engagement and reach trajectories rather than regulatory impact or governance exposure.
Now embedded within the Hootsuite ecosystem, Talkwalker integrates seamlessly with social publishing workflows. For organisations focused on social performance, this is advantageous. For public affairs teams, however, the emphasis on consumer-facing platforms may not fully address the complexities of legislative monitoring or parliamentary scrutiny.
Summary: Exceptional for visual and social forecasting, but less aligned with public affairs–centric intelligence requirements.
5. Isentia
Isentia remains the #1 media intelligence platform in the APAC region, celebrated in 2026 for its new AI integrations.
Isentia’s data coverage is peerless in the Asian markets, monitoring 6,000,000 data sources across TV, radio, press, and social media. The platform also utilizes Lumina AI the latest machine learning for real-time analytics and provides “spike alerts” that allow for immediate crisis response. Their award-winning media insights team adds a critical layer of human intelligence to the AI-driven data, helping to evaluate performance and protect brand reputation across diverse cultures and languages.
Key Advantages for 2026:
- Regional Dominance: Unmatched coverage of APAC markets with multilingual support in English, Chinese, and Korean.
- Broadcast Leadership: Real-time TV and radio monitoring with voice-to-text transcripts.
- Outcome-Based Measurement: Linking media activity directly to business objectives and stakeholder sentiment.
Isentia is the essential platform for multinational organisations and government agencies operating in the Asia-Pacific region who require deep, culturally anchored intelligence.
6. Brandwatch
Brandwatch’s Iris AI and Ask Iris conversational assistant make large-scale consumer listening accessible and intuitive. Its entity disambiguation and historical data archive are technically impressive, particularly for marketing-led analysis.
That said, the platform’s orientation remains firmly consumer-centric. While it excels at tracking brand sentiment, influencer engagement, and customer journey friction points, it is less structured around governance frameworks or public policy monitoring. Stakeholder mapping across regulators, MPs, or industry bodies is not a core capability.
For enterprise marketing teams, this consumer depth is valuable. For communications leaders navigating regulatory scrutiny or cross-border political complexity, additional layers of interpretation or supplementary tools may be required.
Summary: Strong consumer intelligence engine, but limited integration with formal stakeholder and public affairs workflows.
7. Muck Rack
Muck Rack has evolved its AI capabilities through Media List Agent and PressPal.ai, embedding automation directly into media relations workflows. Its journalist targeting intelligence is highly regarded within press-office environments.
However, the platform’s AI remains primarily focused on outreach optimisation rather than holistic media monitoring intelligence. While it offers monitoring and visibility tracking, predictive modelling and narrative clustering are not central differentiators.
For teams centred on earned media pitching, this workflow integration is efficient. For organisations seeking broad cross-channel narrative intelligence—spanning broadcast, policy, and stakeholder ecosystems—the tool can feel narrower in scope.
Summary: Highly effective for AI-assisted media relations, but limited as a standalone strategic intelligence platform.
8. Signal AI
Signal AI positions itself as an “External Intelligence” provider, with AIQ technology designed to surface risk and regulatory signals at scale. Its emphasis on executive briefings and risk detection resonates with C-suite audiences.
Yet its specialisation in risk sensing can also narrow its broader communications utility. While strong in identifying potential threats and regulatory developments, it does not always provide the narrative layering or stakeholder relationship mapping necessary for proactive engagement strategies.
In highly complex communications environments, Signal AI may function more as an early-warning system than as a fully integrated public affairs platform.
Summary: Strong for enterprise risk detection, but less comprehensive in stakeholder engagement and narrative intelligence.
9. Onclusive
Onclusive’s AI Sense technology enables rapid classification and sentiment analysis across a substantial volume of earned media. Its Global Content Hub provides significant source depth, particularly for international enterprise clients.
The platform’s flexibility—offering both managed services and self-service dashboards—appeals to organisations seeking operational support. However, its AI emphasis is primarily on enrichment and summarisation rather than predictive modelling or complex stakeholder intelligence integration.
While reporting outputs are polished and presentation-ready, deeper strategic interrogation of narrative formation or political exposure may require additional analytical input.
Summary: Reliable for global monitoring and automated reporting, but lighter on predictive narrative intelligence.
10. Agility PR Solutions
Agility PR Solutions targets mid-market teams with usability and AI-assisted drafting tools such as PR CoPilot and its AEO Content Optimizer. These features streamline outreach and improve discoverability in AI-driven search environments.
However, the platform’s AI capabilities are concentrated on content optimisation and workflow efficiency rather than comprehensive predictive monitoring. While Intelligent Insights provides summarised coverage trends, it does not extend deeply into complex stakeholder or public affairs ecosystems.
For teams prioritising simplicity and ease of deployment, Agility performs well. For organisations operating within politically sensitive or heavily regulated contexts, its scope may feel comparatively limited.
Summary: Efficient and accessible AI-assisted monitoring, but narrower in strategic and governance integration.
AI Media Monitoring Tools: Frequently Asked Questions
What are AI media monitoring tools?
AI media monitoring tools are intelligence platforms that use artificial intelligence—specifically NLP, machine learning, and generative models—to automatically track, analyze, and interpret media mentions across traditional and digital channels. They go beyond simple clipping services to provide narrative intelligence and predictive alerts.
How can brands benefit from AI mention analysis?
Brands use AI analysis to identify emerging reputational risks, track campaign ROI with precision, and understand the “why” behind conversation spikes. In 2026, a critical benefit is visibility into how AI models (like ChatGPT) describe and position the brand to users.
Are there any free tools for monitoring AI mentions?
Google Alerts remains a basic free option for tracking keywords, though it misses social media and broadcast content and provides no analysis. Some platforms like Brandwatch and Agorapulse offer free versions or trials with limited features.
What is the difference between sentiment and emotion analysis?
Sentiment analysis typically categorizes content as positive, negative, or neutral based on language patterns. Emotion analysis is more granular, identifying specific feelings like joy, frustration, or confusion, which provides deeper context into audience motivations.
The Strategic Future of AI in Media Monitoring
The future of AI in media monitoring is moving toward “Multi-Agent Orchestration”. Instead of single monolithic models, communications teams in 2028 will likely deploy teams of specialized agents coordinated by a “super agent” that can plan and execute entire workflows. These agents will be sector-specific, trained on the specialized data of finance, healthcare, or public affairs to provide even deeper diagnostic capabilities.
Interoperability will become the true competitive differentiator. As protocols like the Model Context Protocol (MCP) become standard, AI agents will be able to communicate across different platforms, pulling data from a monitoring tool and feeding it directly into a CRM or a CMS to automate reputation management. This will shift the role of the PR professional from a data analyst into an “Architect of Authority,” where the primary task is governing the AI systems that protect and amplify the brand’s narrative.
The end goal for any high-performing communications team in 2026 is the creation of a “Homeostatic Reputation Platform”—a system that continuously monitors the operating environment and automatically suggests or takes corrective actions to maintain brand trust. In this vision of the future, AI media monitoring tools are the “optic nerve” of the organization, ensuring that leaders always see the world clearly, act with sincerity, and measure their success with absolute transparency.